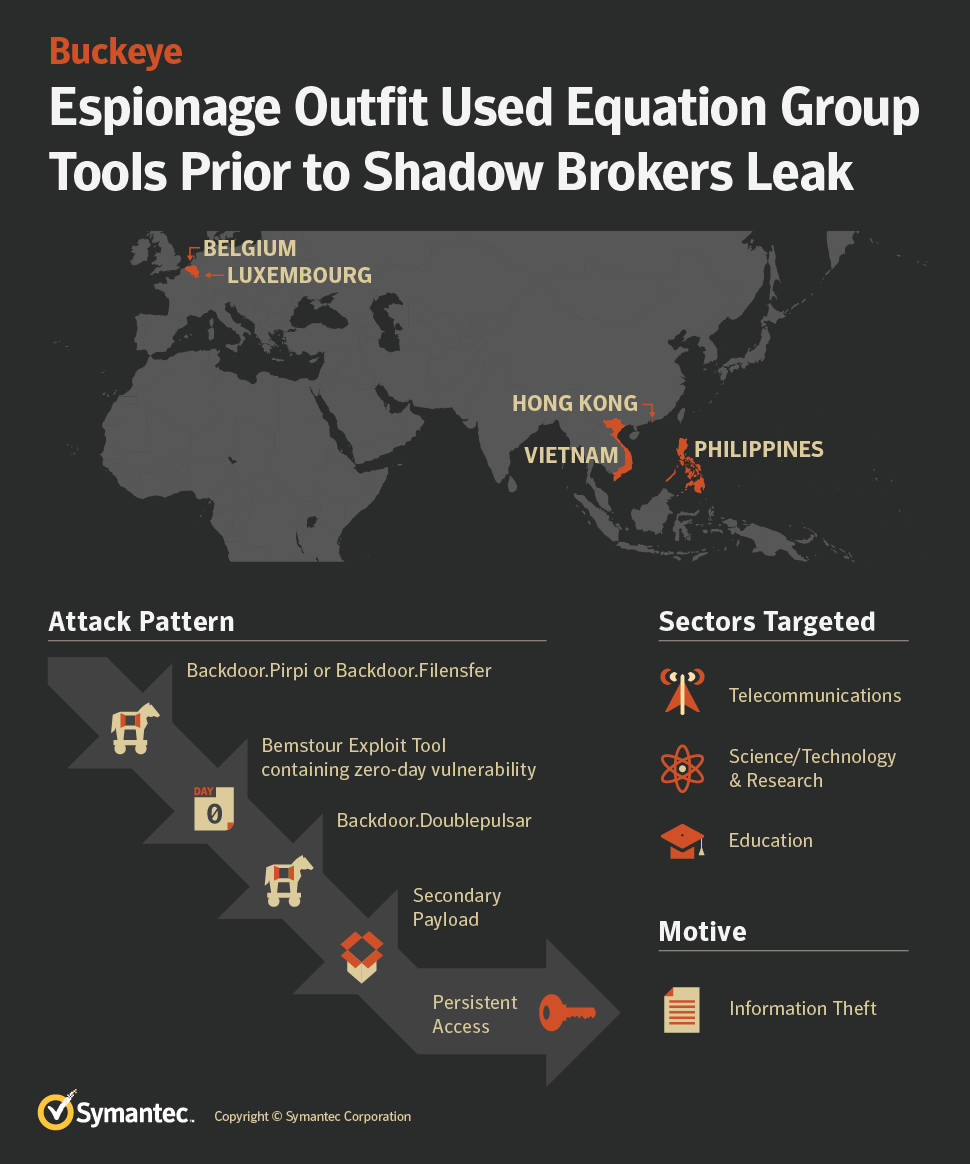
A Chinese hacking group considered to be the “most dangerous” by the NSA stole, copied, or reverse engineered the agency’s own hacking software – then use it against American allies and private companies in Europe and Asia during 2016 attacks, according to researchers with Symantec.
The Chinese hacking group that co-opted the N.S.A.’s tools is considered by the agency’s analysts to be among the most dangerous Chinese contractors it tracks, according to a classified agency memo reviewed by The New York Times. The group is responsible for numerous attacks on some of the most sensitive defense targets inside the United States, including space, satellite and nuclear propulsion technology makers. –New York Times
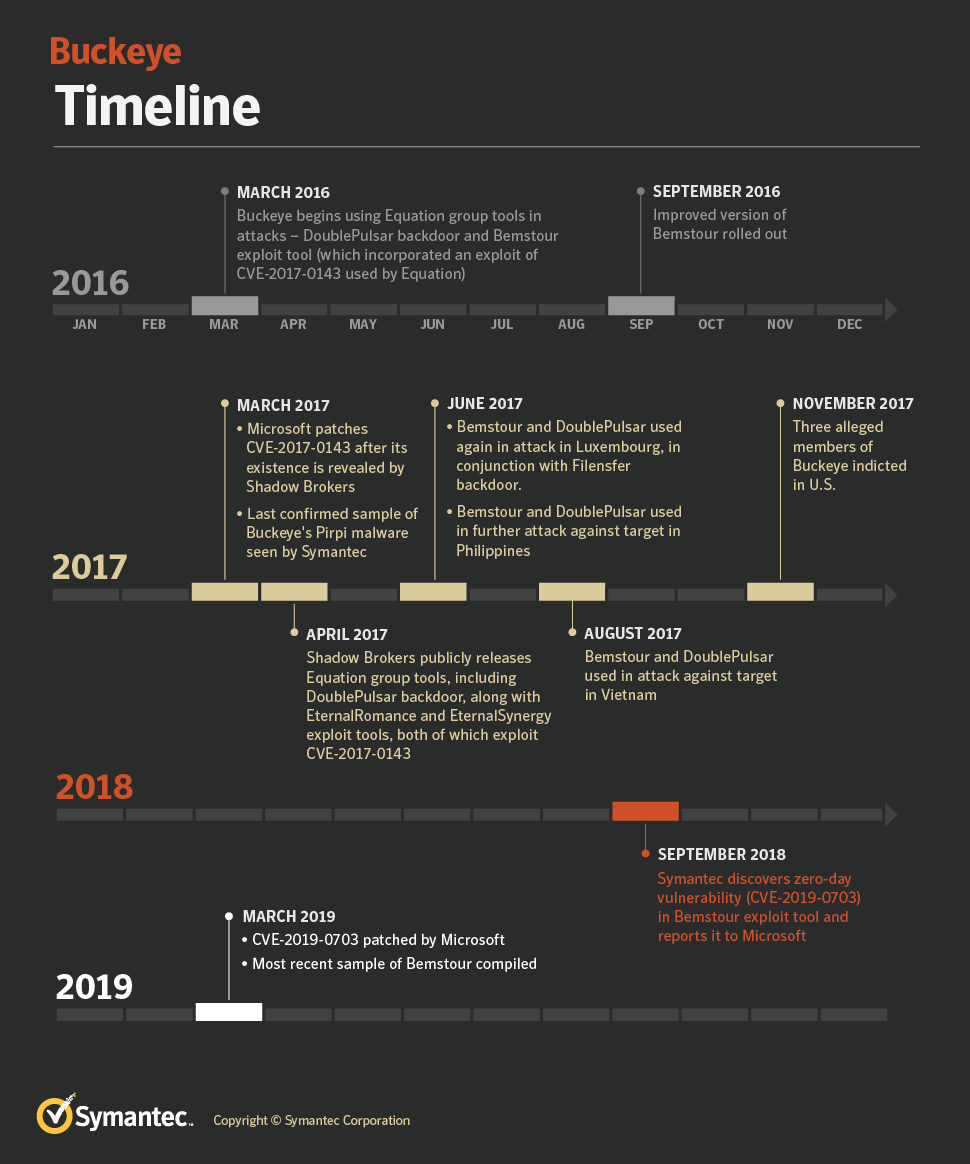
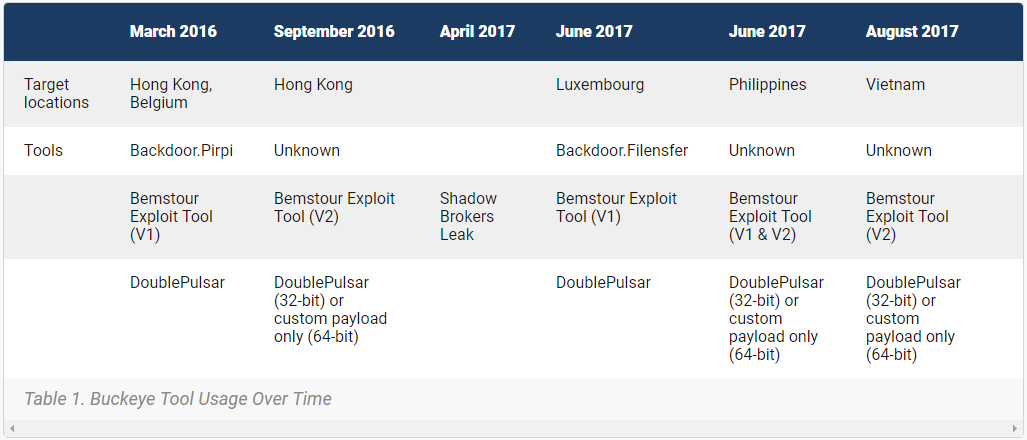
The swiped software (Backdoor.Doublepulsar) and its “custom exploit tool” installation software (Trojan.Bemstour) infects a computer’s memory, and remains even if DoublePulsar is removed. According to Symantec, these tools were used by the Chinese hacking group in 2016 (and shortly after leaked to the public by a group calling itself the Shadow Brokers).
Bemstour exploits two Windows vulnerabilities in order to achieve remote kernel code execution on targeted computers. One vulnerability is a Windows zero-day vulnerability (CVE-2019-0703) discovered by Symantec. The second Windows vulnerability (CVE-2017-0143) was patched in March 2017 after it was discovered to have been used by two exploit tools—EternalRomance and EternalSynergy—that were also released as part of the Shadow Brokers leak.
The zero-day vulnerability allows for the leaking of information and can be exploited in conjunction with other vulnerabilities to attain remote kernel code execution. It was reported by Symantec to Microsoft in September 2018 and was patched on March 12, 2019. –Symantec
Of note – the hackers never used a ‘framework’ tool specifically designed to manage DouplePulsar and other NSA hacking tools, suggesting that the Chinese “only managed to gain access to a limited number of Equation Group tools.”
Symantec identifies the NSA hackers as the “Equation Group,” while the Chinese hackers are known as the “Buckeye group” – identified by the Department of Justice and several cybersecurity firms as a Chinese Ministry of State Security contrator based in Guangzhou. According to Symantec, Buckeye is also known as Advanced Persistent Threat (ATP3) and other names such as Gothic Panda.
Three members of the Buckeye group were indicted by the DOJ in 2017, and while prosecutors do not assert that they are working on behalf of the Chinese government, a classified NSA memo allegedly reviewed by the Times “made clear the group contracted with the Ministry of State Security and had carried out sophisticated attacks on the United States.”
Symantec’s report provides the first evidence that Chinese state-sponsored hackers were able to obtain some of the NSA’s tools before they were later leaked by the Shadow Brokers in August, 2016.
This isn’t the first time US intelligence has had their fancy toys exposed…
Repeatedly over the past decade, American intelligence agencies have had their hacking tools and details about highly classified cybersecurity programs resurface in the hands of other nations or criminal groups.
The N.S.A. used sophisticated malware to destroy Iran’s nuclear centrifuges — and then saw the same code proliferate around the world, doing damage to random targets, including American business giants like Chevron. Details of secret American cybersecurity programs were disclosed to journalists by Edward J. Snowden, a former N.S.A. contractor now living in exile in Moscow. A collection of C.I.A. cyberweapons, allegedly leaked by an insider, was posted on WikiLeaks. –NYT
The 2017 Wikileaks “Vault 7” release of documents related to CIA hacking and electronic surveillance tools was an embarrassing leak for the agency.
The series of 24 documents which began to publish on March 7, 2017 – reveal that the CIA had a wide variety of tools to use against adversaries, including the ability to “spoof” its malware to appear as though it was created by a foreign intelligence agency, as well as the ability to take control of Samsung Smart TV’s and surveil a target using a “Fake Off” mode in which they appear to be powered down while eavesdropping.
Joshua Adam Schulte, 29, a former employee in the CIA’s Engineering Development Group, is believed to have provided the agency’s top-secret cyber warfare tools to WikiLeaks – according to a disclosure by federal prosecutors at a January hearing in a Manhattan court on unrelated charges of possessing, receiving and transporting child pornography. Schulte, who has been in jail for months, has pleaded not guilty on the child porn charges.
Schulte previously worked for the NSA before joining the CIA, then “left the intelligence community in 2016 and took a job in the private sector,” according to a statement reviewed by The Washington Post. He has been detained at the Metropolitan Correctional Center in Manhattan since December, 2017.
via ZeroHedge News http://bit.ly/2VaOked Tyler Durden