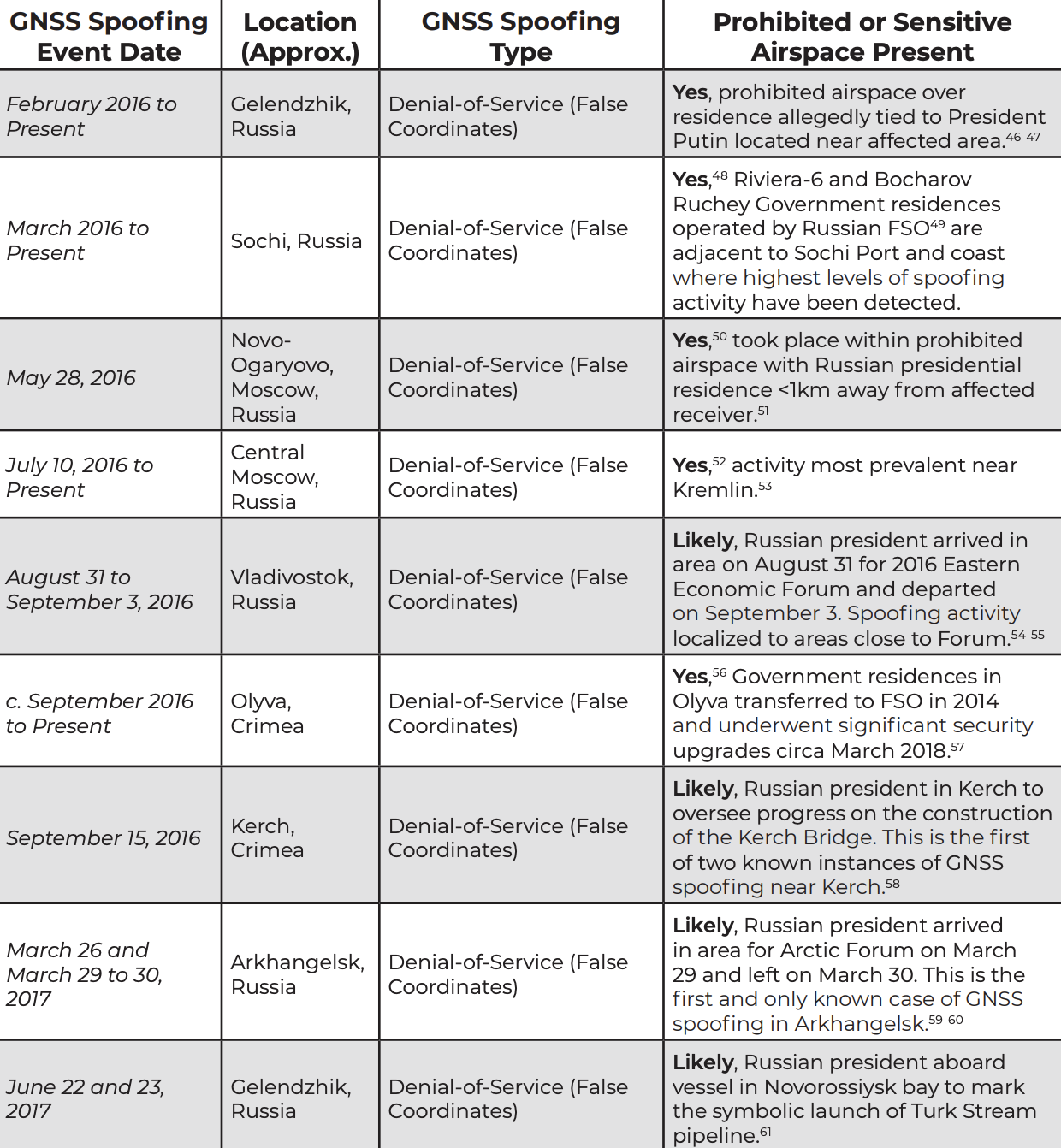
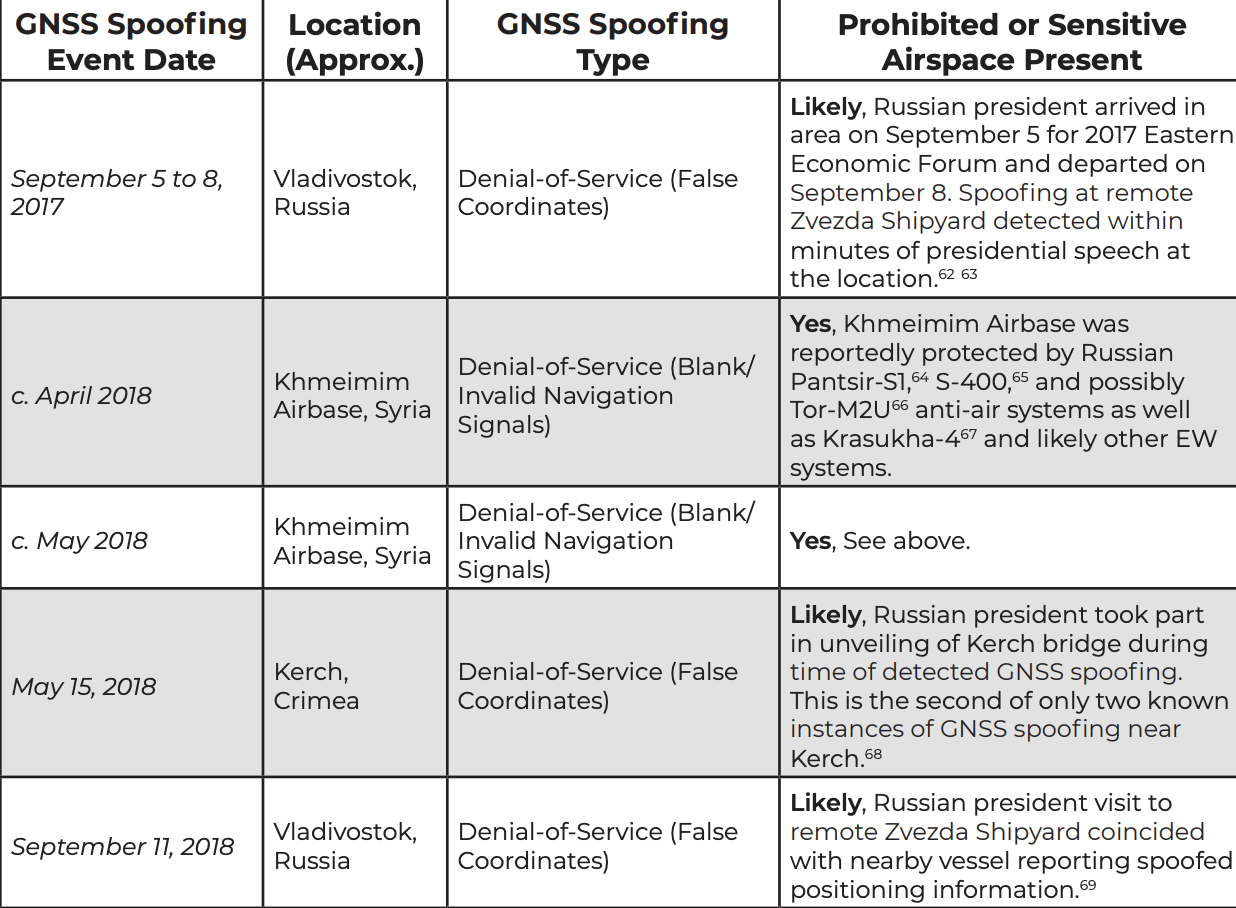
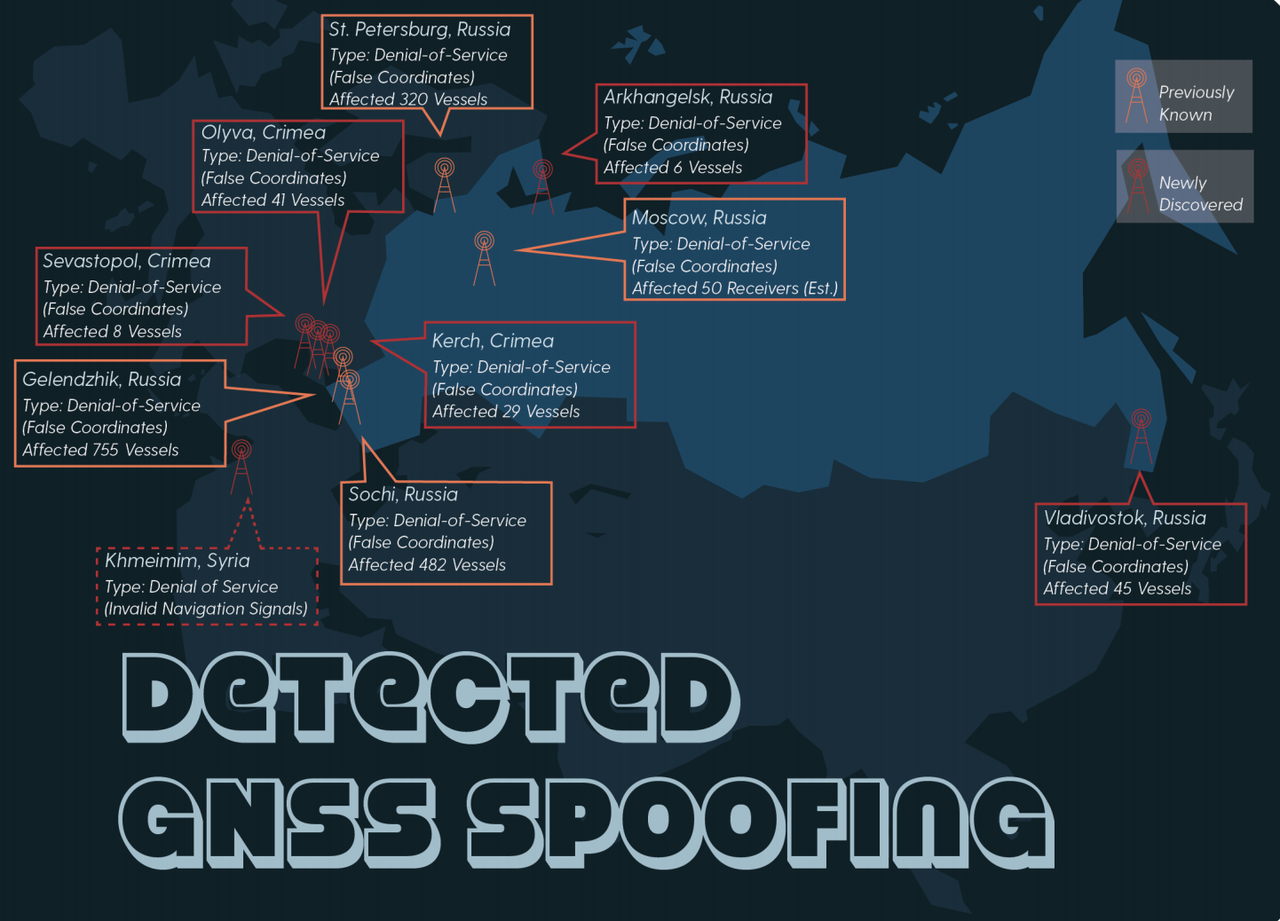
A study published by the Center for Advanced Defense has determined that the Russia security services are using a cutting-edge new technique, presumably to protect President Putin – as well as several government buildings in Russia, and military facilities in Syria – from drone attacks.
Using publicly available data sets and reports on social media and in the press, the organization pinpointed incidences of “GPS spoofing” when an electronic weapon scrambles the data stream between nearby ships, vehicles and aircraft and the satellites that help power their navigation systems. In many cases, like one incident that occurred near the Kerch Strait, the site of a skirmish late last year between Ukrainian and Russian forces. As Putin and a convoy of construction vehicles crossed a new bridge over the Strait, the GPS of ships docked in a nearby harbor suddenly went “haywire.”
Here’s more on that from CBS News:
The ships’ GPS systems suddenly began to indicate they were actually 65 kilometers away, on land, in the middle of an airport.
The incident is one of many highlighted in a new report that found the Kremlin “spoofed” global positioning systems, or GPS, to effectively place a bubble around Putin or properties associated with him. The researchers, with a nonprofit called C4ADS and the University of Texas at Austin, used public marine GPS databases, as well as a GPS monitoring device on the International Space Station to track similar instances.
The report, which documented a pattern of spoofing surrounding the movements of the Russian head of state…
….surmised that the GPS scrambling technology was employed to protect him against drone attacks, or airborne robot spies.
The researchers theorize that one reason “spoofing” is deployed is to protect Putin and other Russian officials from attacks or surveillance by drones that rely on GPS.
“The purpose of this spoofing activity was likely to prevent unauthorized civilian drone activity as a VIP protection measure,” they wrote in the study.
The report also identified buildings used by Russian security services or the president that appeared to be hotspots for spoofing activity, and detailed several incidents of suspected mass-spoofing activity.
While the technology was presumably employed to protect Putin, there is an inadvertent drawback that could be used by exploited by malicious actors to stalk the president.
However, there’s a drawback to creating a GPS bubble around a world leader, said Todd Humphreys, an engineering professor at the University of Texas at Austin, who was involved with the study. It also makes it easier to keep track of Putin.
“What’s ironic is if you look at these patterns, and if you coordinate it with the movements of the leader of Russia, it appears you have a Putin detector,” Humphreys said. In other words, if you detect spoofing, there’s a good chance Putin may be nearby.
It also creates the possibility for collateral damage.
The technique could also prove dangerous. The 24 maritime vessels that reported the Kerch bridge incident were otherwise unaffected. But Humphreys said a similar tactic in Syria could affect airplanes, which require functioning GPS to stay out of harm’s way.
The researchers identified Russian equipment in Syria emitting what Humphreys described as “a whole different signal, one that was much much stronger, but not spoofing.” The signal appeared to be jamming airplane GPS units, effectively rendering their navigation systems inoperable.
When the same tactic was apparently deployed during large-scale Russian military exercises in eastern Europe, civilians saw the effects, according to the report.
“Norway and Finland reported severe GPS outages affecting commercial airliners and cell phone networks for several days,” according to the report.
Unfortunately, this drawback would probably exclude GPS spoofing from the list of possible anti-drone techniques employed by airports…we imagine the security staff at Heathrow and Gatwick will be very disappointed.
via ZeroHedge News http://bit.ly/2Uz76Qt Tyler Durden