Company Weaponizes Soldiers’ Smartphone Data To Expose US Military Secrets
As pressure mounts on Big Tech firms to curb their invasive data-harvesting practices first implemented to cultivate valuable personal data that can be packaged and sold to advertisers for a premium (indeed, this is how the “free Internet” was built), WSJ has just published a shocking story about how one firm (a defense contractor called “PlanetRisk”) discovered it could track sensitive movements of American troops in Syria via data generated by apps on their smartphones.
After making the discovery, the firm used the data to build a surveillance tool that could monitor the travel of refugees from Syria to Europe and the US. The goal was to sell the finished product to the counter-terrorism and intelligence communities.
But, as WSJ pointed out, “buried in the data was evidence of sensitive US military operations by American special-operations forces in Syria.”
The fear now is that this data can be bought and sold by America’s adversaries to gain valuable intelligence insights into the movements of American forces. Many vendors now sell “global location information from mobile phones to intelligence, military and law-enforcement organizations.” The US has struggled to effectively monitor what “software service members are installing on devices and whether that software is secure.”
“Our country’s intelligence leaders have made it clear that putting Americans’ sensitive information in the hands of unfriendly foreign governments is a major risk to national security,” he said.
This isn’t a new issue. Back in 2019, the Trump Administration moved to force the divestiture of Grindr, the LGBTQ-friendly dating app, which the military and CFIUS – the Commerce Department’s board that reviews foreign deals – largely over concerns that data gleaned from the app might be weaponized to track US troops.
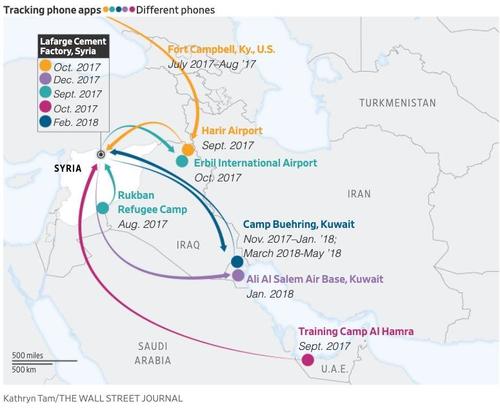
What PlanetRisk revealed could easily be replicated by an American adversary. The company simply traced cell signals from US bases in Syria to an abandoned cement factory back in 2016. This was before US special forces use of the area as a staging ground had become public knowledge. What’s more, PlanetRisk could monitor the movements of American troops even while they were out on patrol, a serious operational security risk that opened units up to being targeted by enemy forces.
When PlanetRisk traced telephone signals from US bases to the Syrian cement factory in 2016, it hadn’t been disclosed publicly that the factory was being used as a staging area for U.S. and allied forces.
PlanetRisk resolved to use its discovery to build a new tool and sell it to intelligence agencies, but it was beaten to market by a competitor and the firm eventually dissolved. But in its reporting, WSJ managed to replicate PlanetRisk’s findings, tracking movements at the same cement factory in 2017 and 2018 from a commercial data broker and analytics company that wished to remain anonymous. The Journal tracked the movements of people who appeared to be American special ops, just as PlanetRisk had.
WSJ also tracked the data to US facilities such as Fort Bragg, Fort Hood in Texas or tiny desert outposts such as the US-run Camp Buehring in Kuwait before later traveling to the Lafarge Cement Factory in northern Syria. Although these data sets don’t contain personalized names, each individual is assigned an alphanumeric identifier designed for advertisers. But, as WSJ points out, the places associated with a device can offer clues that can in turn be weaponized. While the US has allowed personal data to become a commodity – which led to the backlash in 2018 and 2019 in the wake of the Facebook-Cambridge Analytica scandal.
Source: WSJ
While the US government has taken steps to teach operational security best practices to troops, there’s little doubt that the US system’s approach to commercializing data on behalf of the advertising and technology industries has created massive security holes. And unsurprisingly, China is getting better at exploiting them, while at the same time banning the export of data on its own citizens to prevent any rival countries from tracking its citizens and military personnel in the same way.
Tyler Durden
Mon, 04/26/2021 – 23:40
via ZeroHedge News https://ift.tt/3nqCFaV Tyler Durden