DOJ Targets Crypto Crooks As Ransomware Investigations Elevated To Same Level As Terrorism
The Department of Justice is set to announce the recovery of some $4.4 million dollars in cryptocurrency paid in ransom to hackers who prompted the shutdown of the Colonial Pipeline, according to CNN, which notes that “The ransom recovery is a rare outcome for a company that has fallen victim to a debilitating cyberattack in the booming criminal business of ransomware.”
Colonial Pipeline Co. CEO Joseph Blount told The Wall Street Journal In an interview published last month that the company complied with the $4.4 million ransom demand because officials didn’t know the extent of the intrusion by hackers and how long it would take to restore operations.
But behind the scenes, the company had taken early steps to notify the FBI and followed instructions that helped investigators track the payment to a cryptocurrency wallet used by the hackers, believed to be based in Russia. US officials have linked the Colonial attack to a criminal hacking group known as Darkside that is said to share its malware tools with other criminal hackers. -CNN
The Monday announcement is part of a new initiative by Justice Department to crack down on all types of federal cyber crimes – including botnets, money laundering and ‘bulletproof hosting,’ according to Ars Technica. The move will elevate ransomware investigations to the same level as that of terrorism.
“To ensure we can make necessary connections across national and global cases and investigations… we must enhance and centralize our internal tracking of investigations and prosecutions of ransomware groups and the infrastructure and networks that allow the threats to persist,” said Deputy Attorney General Lisa Moreno in a Thursday memo first reported by Reuters.
According to the Ars: The new directive applies not just to cases or investigations involving ransomware but a host of related scourges, including:
- Counter anti-virus services
- Illicit online forums or marketplaces
- Cryptocurrency exchanges
- Bulletproof hosting services
- Botnets
- Online money laundering services
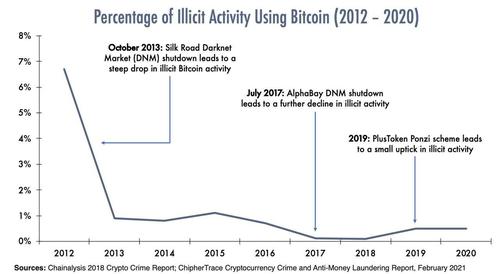
We expect crypto regulation to be a central focus, despite the fact that the role of digital currencies in illicit activity has basically bottomed out, while the fear-mongering crypto narrative has been thoroughly BTFO (by a former CIA director no less).
The Biden DOJ’s push to target cybercriminals comes not only after the Colonial pipeline hack, but a May attack three weeks later at meat producer JBS, along with several other hacks across various industries – including Scripps Health, which continues to recover after taking their electronic health records offline for weeks.
Meanwhile, US prosecutors charged a 55-year-old Latvian woman in a ‘Trickbot Gang’ case – the first test of the DOJ’s Ransomware and Digital Extortion Task Force according to a press release cited by cybersecurity professional Shah Sheikh.
US Prosecutors Charge Latvian Woman in Trickbot Gang Case: Case Is First Test for DOJ’s Ransomware and Digital Extortion Task Force U.S. Justice Department prosecutors have charged a 55-year-old Latvian woman with helping to develop code for the Trickbot… https://t.co/h5JLwQ1Wxk pic.twitter.com/PVHqveAAi8
— Shah Sheikh (@shah_sheikh) June 7, 2021
More via Ars Technica:
By using an ad-hoc group to track cases centrally, Justice Department officials hope the move brings focus and consistency to the investigations it conducts and cases it brings.
On Thursday, at least two new ransomware infections surfaced. The first struck Cox Media Group and, according to The Record, left the media company unable to provide livestreaming for TV stations and internal networks. The second hit UF Health Central Florida, which operates two hospitals. A spokesman for UF Health said that access to email and most other system platforms had been suspended. Staff in all hospitals and physician clinics are now using pen and paper to document and order care.
We can feel the undoubtedly upcoming crypto regulations in our bones.
Watch Live (stream will begin airing at 3:15 ET):
Tyler Durden
Mon, 06/07/2021 – 15:05
via ZeroHedge News https://ift.tt/34ZyfPY Tyler Durden