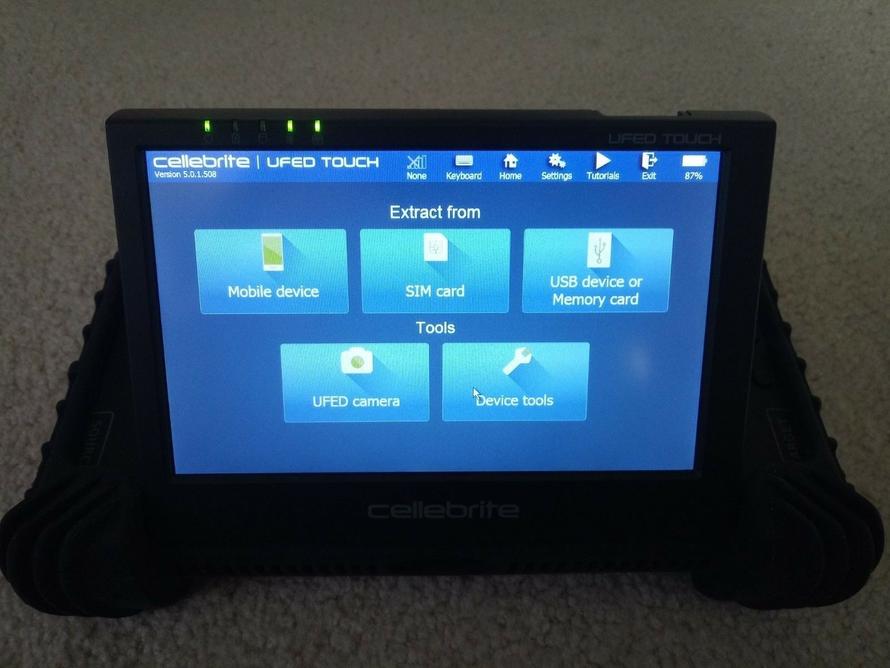
A valuable piece of Israeli-made technology used by police around the world to crack into iPhones, Android devices and other modern mobile devices have been popping up on Ebay – often containing private data after sellers have failed to properly wipe them, according to Forbes.
When eBay merchant Mr. Balaj was looking through a pile of hi-fi junk at an auction in the U.K., he came across an odd-looking device. Easily mistaken for a child’s tablet, it had the word “Cellebrite” written on it. To Mr. Balaj, it appeared to be a worthless piece of electronic flotsam, so he left it in his garage to gather dust for eight months.
But recently he’s learned just what he had his hands on: a valuable, Israeli-made piece of technology called the Cellebrite UFED. –Forbes
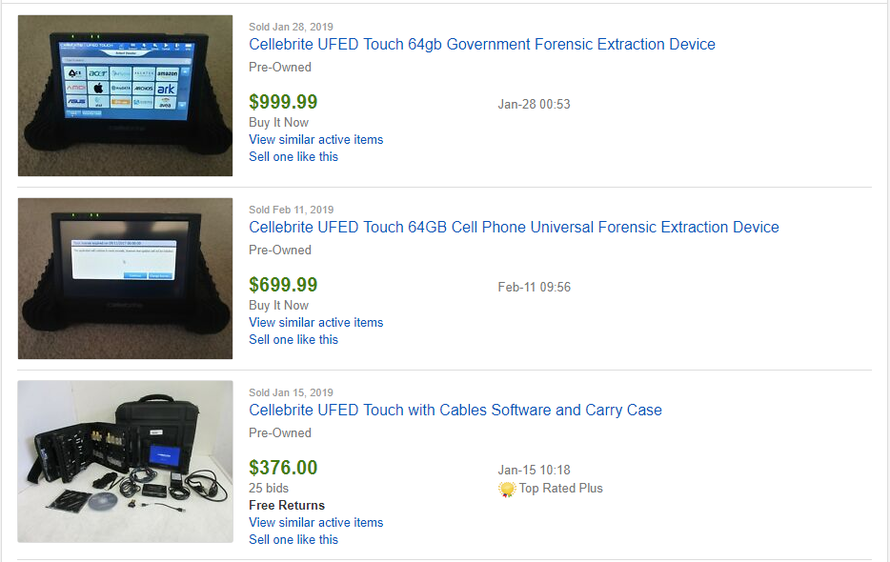
Cellebrite has landed millions in federal contracts for their technology; from the FBI to Immigration and Customs Enforcement – but Ebay buyers have been acquiring the tablet-style cracking devices for between $100 and $1,000. Brand new, Cellebrite units start at $6,000.
Cellebrite, meanwhile, is not happy.
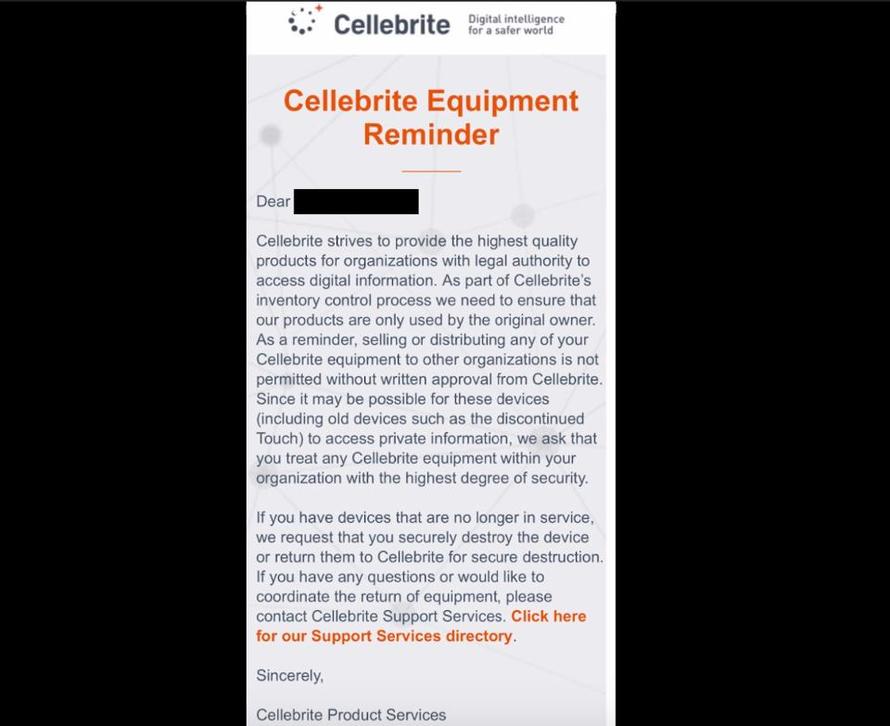
On Tuesday, two sources from the forensics industry passed Forbes a letter from Cellebrite warning customers about reselling its hugely popular hacking devices because they could be used to access individuals’ private data. Rather than return the UFEDs to Cellebrite so they can be properly decommissioned, it appears police or other individuals who’ve acquired the machines are flogging them and failing to properly wipe them. Cybersecurity researchers are now warning that valuable case data and powerful police hacking tools could have leaked as a result. –Forbes
Cybersecurity expert and Hacker House training academy founder Matthew Hickey conducted an experiment last month in which he bought a dozen such units to test. What he found on the secondhand kits was disturbing – as they contained information on what devices searched, along with what types of data were removed and mobile identification information such as the IMEI code.
He was also able to find what appeared to be Wi-Fi passwords which could have belonged to either police agencies or private entities which used the devices, such as independent investigators or business auditors.
Hickey believes he could have extracted more personal information, such as contact lists or chats, though he decided not to delve into such data. “I would feel a little awful if there was a picture of a crime scene or something,” he said. But using the information within a UFED, Hickey believes a malicious hacker could identify the suspects and their relevant cases.
In one screenshot provided by Hickey to Forbes, the previous UFED user had raided phones from Samsung, LG, ZTE and Motorola. Hickey had tested it on old iPhone and an iPod models with success. –Forbes
“You’d think a forensics device used by law enforcement would be wiped before resale. The sheer volume of these units appearing online is indicative that some may not be renewing Cellebrite and disposing of the units elsewhere,” Hickey told Forbes.
“Units are intended to be returned to vendor precisely for this reason, people ignoring that risk information on the units being available to third parties.”
Cellebrite uses encrypted software exploits to crack into mobile phones – often kept secret from manufacturers such as Apple and Google, according to Hickey. The company’s devices are so good at finding their way into iOS devices that they were able to crack the passcodes of even the latest Apple models, up to the iPhone X.
Apple, meanwhile, is in a constant race with Cellebrite to find and patch the flaws.
via ZeroHedge News https://ift.tt/2EGzkzN Tyler Durden